Identity Federation
Before Identity Federation, lets talk about How are we accessing resources in Cloud
Accessing resources in Cloud
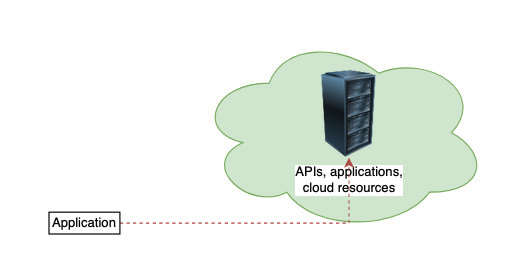
Note: Application needs access to consume the above resources
Examples of above diagram
- Application running in on-prem accessing GCP resources (like gcs bucket, container registry, S3, vault, etc)
- Application running in other cloud accessing GCP resources
- Github actions trying to deploy/create resources in Azure
- Jenkins running in Kubernetes trying to deploy things to AWS
- Application running in GCP cloud function trying to access to aws resource
Using Identities of that cloud
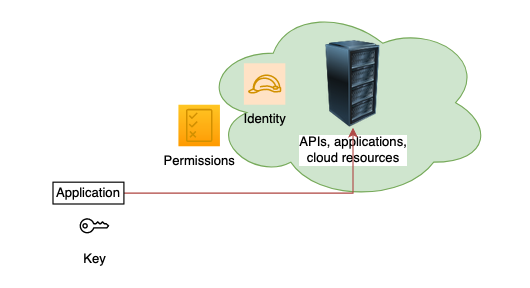
- Create an Identity
- Attach permissions
- Create key/secret/token for that identity
- Share the key with application
What are the problems of using cloud identity outside that cloud ?
- If there is expiration for key/secret/token, then rotating it
- create new keys in cloud
- deploy/restart the all the applications (with their replicas) in proper order
- remove the old keys in cloud
- If no expiration, static keys
- Not only the configured application, anyone with key can access it
- Developer can copy the key and use it from their local machine
- Developer can share the keys with co-workers (co-worker can also become ex-co-worker)
It became Secret management problem from Identity/Access management problem
How will we do it, if the application is in the same cloud ?
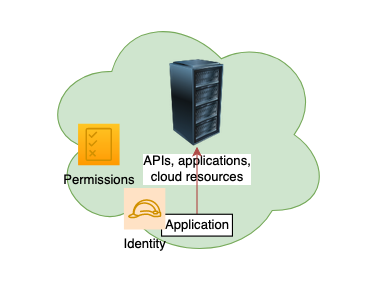
- Attach Identity to that resource
Keyless authentication is the key 🙃
Identity Federation
- What if we are able to use same identity across clouds.
- What if we are able to use one identity to exchange the another identity for limited period
That is what Identity federation is.
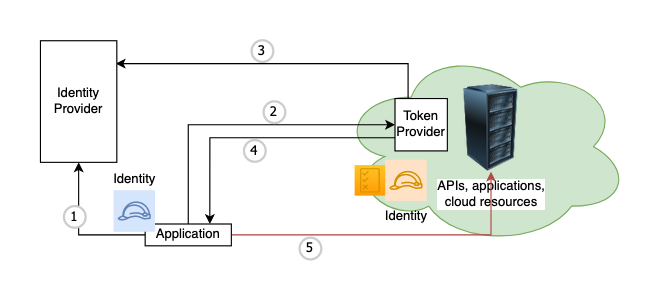
- Application get Identity key/secret/token from its own local Identity Provider
- Each cloud will have its own Identity Provider
- Example custom Identity Provider: https://github.com/dexidp/dex
- Application sends this Identity key/secret/token to the destination cloud’s Token Provider
- Token Provider will validate this Identity key/secret/token against application’s Identity Provider
- Application’s Identity Provider should be preconfigured in cloud’s Token Provider
- Example Token Providers
- Token Provider will issue a short lived token to Application
- The token will have permission/role based on preconfigured values
- Now, application can use to access resources in cloud
Examples:
- Deploy infra in google cloud using github actions (with github token). Refer
- Deploy infra in aws cloud using github actions (with github token). Refer
- Kubernetes pods access Vault using kubernetes service accounts. Refer
- Assume an AWS Role from a Google Cloud Instances without IAM keys. Refer
- Allow EC2 instance to access google container registry. Refer
- Allow particular instance of EC2 instance to talk to vault. Refer